Cloud Security
Implement and operate safely within public or private cloud service providers.






Looking to safeguard your cloud environment throughout the whole life cycle?
At Netdata, we help you protect the access points, the perimeter, and infrastructure in hybrid and multi-cloud environments, complying with security policies and taking full advantage of all capabilities.

Cloud security issues?
We have an overview of the most common cases that can trigger a cybersecurity breach.
Complexity
The complexity of multi-cloud environments, the lack of information and the need of an expert team might slow down cloud projects.
Lack of visibility
The Shadow IT and service adoption put on burden to identify and protect your attack surface.
Speed
Traditional cloud security tools are unable to keep the required pace for DevOps teams.
Be safe with a more secure and resilient cloud environment
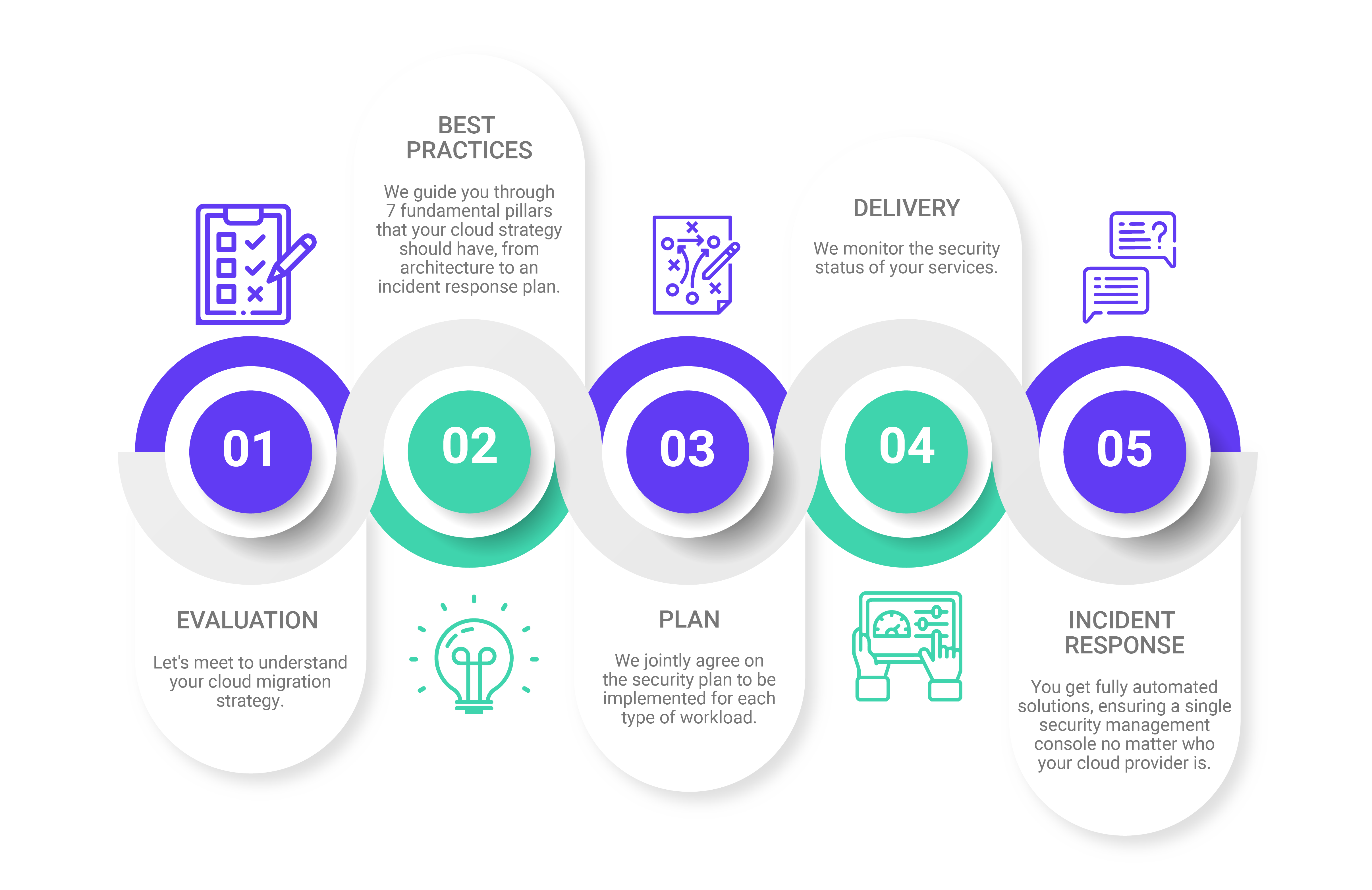
5 steps for cloud security
Our success cases
We've implemented SaaS model in record time
"We implemented more than 4000 VPN´s within a week without having to purchase a single equipment. Besides 60% of our people were able to work during COVID-19 from home with full access to their applications".
José Mejía
![]()






